If you have already transitioned all mailboxes to Exchange Online what’s next? Can you remove all your on-premise Exchange infrastructure? What about Microsoft Entra ID Connect (new Entra Connect) and on-premise Active Directory?
When Microsoft Entra ID Connect sync is enabled, objects are synchronized from on-premises to the cloud, and changing attributes in Azure (Microsoft Entra ID) is not allowed. Instead, those attributes need to be modified in on-premise AD. This requirement is true whether you run Exchange Hybrid because your on-premises Active Directory Forests / Domains remain the source of truth for objects synchronized to Microsoft Entra ID (Microsoft Entra ID) including the email “attribute-set”. Most attributes that are synced from on-premise AD are read-only in Microsoft Entra ID (Microsoft Entra ID) and must only be modified in on-premise AD or Exchange.
Microsoft Entra ID Connect does not have full-scale write-back capabilities, and any scenario where attribute updates are allowed in the cloud will result in a stale set of attributes in AD which only calls for troubles. And if you disable Microsoft Entra ID Connect Sync, then you can finally remove on-premise Exchange but end up with the task of managing two identities (including passwords!) – on-premise and in the cloud which is not a very Admin-friendly approach, to say the least.
The best master plan that many companies are following these days is to entirely remove dependency on your on-premise AD, and this is a long-term and significant strategic undertaking. Until then, the short-term goal should be to de-emphasize on-premise Exchange infrastructure. As of recently, there’s now a “soft” way available for trimming down the on-premise Exchange environment where you shut down (not remove!) the last on-premise Exchange server and install the “ExchangeManagement Tools” role anywhere on the member server or even client OS which allows proper on-premise Exchange attribute handling. There is also some more substantial Exchange on-premise cleanup possible to permanently get rid of Exchange AD footprint as explained in the below Microsoft article.
Manage recipients in Exchange Server 2019 Hybrid environments | Microsoft Learn
“An updated version of the Exchange Management Tools can eliminate the need for running an on-premises Exchange server if all of the following statements are true:
- You migrated all mailboxes and public folders to Exchange Online (no on-premises Exchange recipients).
- You use AD for recipient management and cloud sync or Microsoft Entra Connect for synchronization.
- You don’t use or require the on-premises Exchange admin center or Exchange role-based access control (RBAC).
- You’re comfortable using Windows PowerShell only for recipient management.
- You don’t require auditing or logging of recipient management activity.
- You’re running only one on-premises Exchange server and only for recipient management.
- You want to manage recipients without running any Exchange servers.
Use Exchange Setup in Exchange 2019 Cumulative Update 12 or later to install the latest Management tools on any domain-joined computer (client or server). For instructions, see Install the Exchange Management tools.
Once you shut down the last Exchange server, Exchange RBAC will no longer function. Users who were a part of Exchange Recipient groups or had custom Exchange roles allowing for recipient management will no longer have permission. Only domain admins and users who are assigned permission to use the Add-PermissionForEMT.ps1 script will be able to perform recipient management.
Once you shut down your last Exchange server and perform the Exchange hybrid and Active Directory cleanup steps as previously described, you should erase and reformat your last Exchange server. Do Not Uninstall the Exchange Server.”
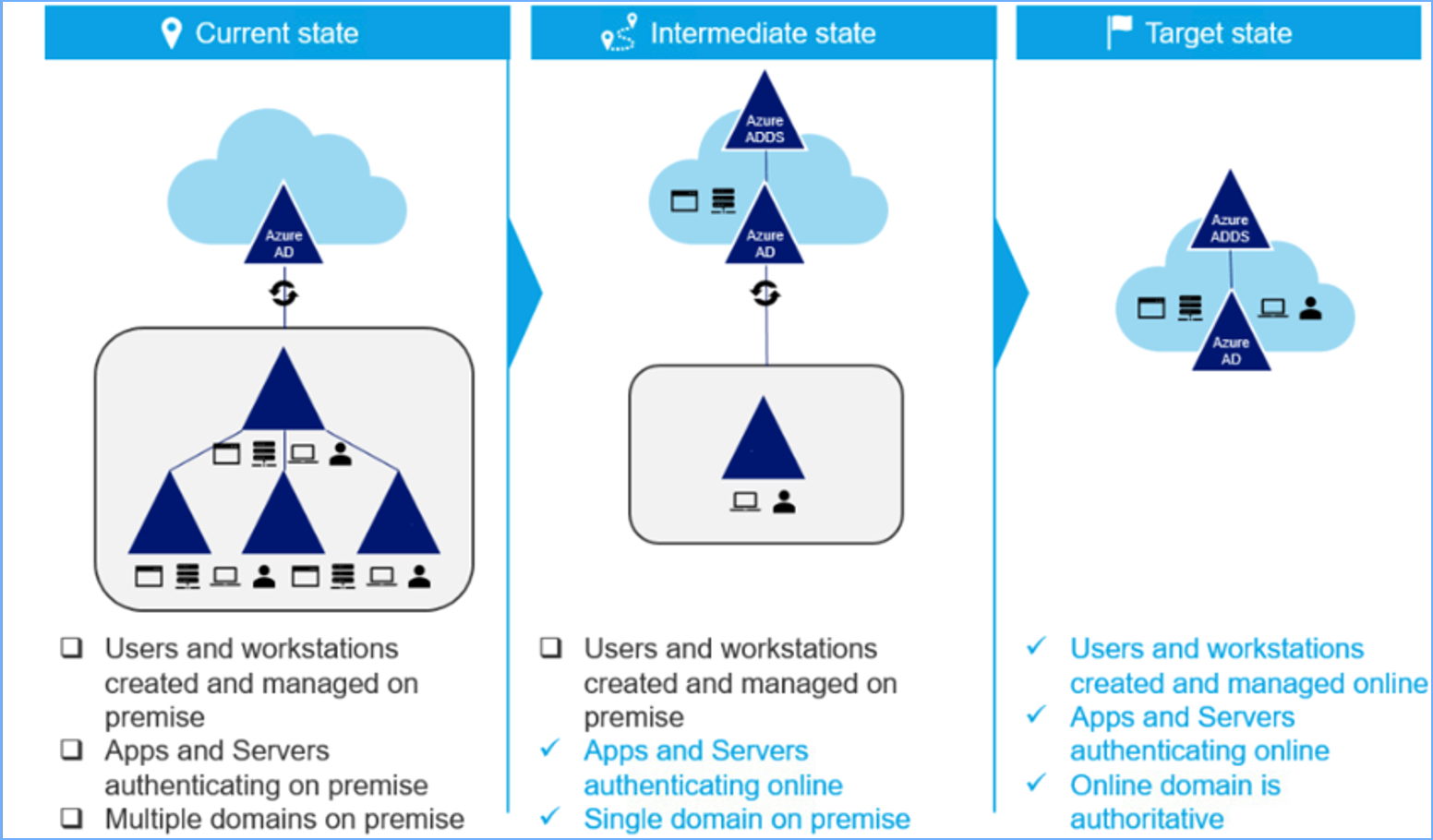
Here are high-level steps to summarize all the above:
-
Messaging / Exchange Hybrid
- Deploy new “Exchange Management Tools” to manage mail object attributes locally
- Remove the on-premise messaging environment per the Microsoft article
- Optionally: Perform Exchange objects cleanup per Microsoft article
-
Directory / Microsoft Entra ID Connect
- Move all your on-premise servers to Azure
- Deploy Microsoft Entra ID DS (Microsoft’s managed legacy AD analogue) for legacy AD functions, mainly app dependencies for Kerberos authentication
- Cut off all your app on-premise AD dependencies towards Microsoft Entra ID DS or new Azure (Microsoft Entra ID)
- Disable Microsoft Entra ID Connect and go to the Full Online identity management approach
- De-commission on-premise AD